The identical week in late February that Russian troops rolled into Ukraine, one of many world's most potent Kremlin-aligned hacking gangs threatened to assault the U.S. and NATO allies. The so-called Conti group, infamous for its use of ransomware to extort thousands and thousands from hospitals and emergency providers, now threatened to focus on America's crucial infrastructure — very important methods like the facility grid and water provide.
For 3 tense days, cyber-defense professionals anxiously anticipated the group's subsequent transfer. Then, with little warning, the gang blew up.
Conti's community was allegedly infiltrated by a Ukrainian safety researcher who leaked the group's secrets and techniques on Twitter, together with its chat data, ransomware code and monetary particulars. The leak revealed that Conti was disorganized and vulnerable to inside squabbles. They have been additionally one of the worthwhile hacking crews on the planet.
"Ransomware-as-a-service," often called RaaS, has exploded in recognition lately, with prison gangs raking in money extorted from well being care suppliers, retailers, producers, faculties, native governments and plenty of different organizations. Such schemes shot up up 85% final yr from 2020, and particular person calls for elevated 144% to $2.2 million. The typical fee was up 78%, to roughly $541,000, in response to a brand new report by Unit 42, a risk analysis staff at Palo Alto Networks.
"The overwhelming majority of ransomware actors are financially motivated. RaaS makes finishing up assaults considerably simpler by decreasing the barrier to entry and increasing the attain of ransomware," Unit 42's Ryan Olson advised CBS Information. "As organizations proceed to pay ransoms, the extra these actors put money into their ransomware organizations and are fueled to proceed their efforts."
Many hacking teams function like a enterprise that's run "for criminals, by criminals, with agreements that set phrases, usually in change for month-to-month charges or a proportion of ransoms paid," Olson stated, including that the teams usually are compartmentalized with departments targeted on duties like administration, coding, advertising and marketing and safety testing.
These three organizations accounted for greater than a 3rd of ransomware exercise final yr:
Conti
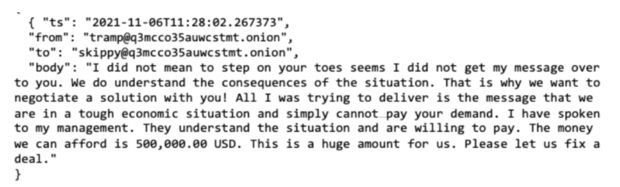
Conti's progress was astronomical and unprecedented, Olson stated. Within the two years previous to the leaks that led to the group's implosion, their actions surged. Conti was liable for extra safety incidents than some other ransomware gang. The group stole and publicly launched personal info from over 600 corporations and authorities organizations. Their common ransom demand rose from simply $178,000 in early 2020 to just about $1.8 million final yr.
"They're ruthless," Olson stated, noting the group's willingness to go after extra susceptible targets like hospitals, well being care suppliers, municipal governments and legislation enforcement businesses. "They function with out a code of honor."
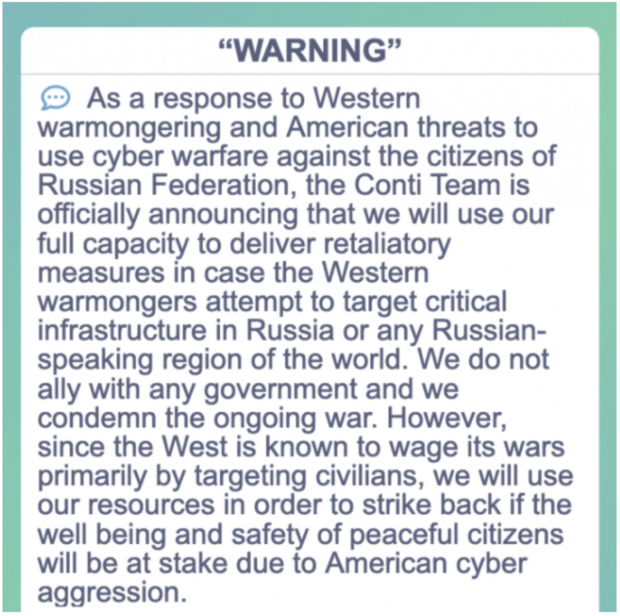
On a darkish net discussion board in February, Conti introduced its "full help" of the Russian authorities and threatened to make use of its "full capability to ship retaliatory measures" if NATO allies focused Russian infrastructure with cyberattacks.
REvil
REvil is greatest recognized for demanding $70 million in 2021 from software program infrastructure supplier Kaseya — the most important ransomware assault on report. The group pioneered ransomware-as-a-service, a enterprise mannequin that permits cybercriminals to promote their hacking experience and launch assaults utilizing their very own explicit ransomware software program.
REvil's software program would infect and lock networked workplace workstations, usually shutting down the focused enterprise till a ransom demand was paid. REvil's calls for various, relying on the dimensions of the corporate and sort of knowledge stolen. If an organization didn't pay, REvil would double their ransom calls for and publish the stolen knowledge. Unit 42 analysts discovered that REvil's common demand in 2021 jumped to $2.2 million, greater than 4 occasions the $500,000 it had requested for beforehand. Their highest ransom demand final yr was $5.4 million.
The group was allegedly dismantled just lately by Russia's inside safety company on the request of a number of worldwide legislation enforcement businesses, together with U.S. authorities.
HelloKitty
The HelloKitty group is likely to be much less well-known than rival ransomware gangs, however they're pioneers. In early 2020 a Linux-variant of its ransomware focused VMWare's software program utilized in knowledge facilities. HelloKitty is greatest recognized for allegedly having stolen and launched supply code from Polish online game developer CD Projekt Pink.
The gang, also called FiveHands, favored company targets and used a multipronged assault, usually threatening to launch stolen knowledge on the darkish net and hammering victims with denial of service assaults if ransom calls for weren't met. Legislation enforcement businesses imagine that previous to the Russian invasion, the group operated from jap Ukraine.
Whereas not as financially profitable as different main ransomware gangs, HelloKitty's techniques and tech have been progressive, inspiring extra well-known ransomware operators.
"Cybercrime is a cat-and-mouse recreation," Olson stated "There are at all times methods to cease attackers from being profitable. Nonetheless attackers will proceed to evolve and innovate their techniques. It's important to be ready and educated on the newest threats so you know the way to guard your group."